Difference between revisions of "Authentication With MFA"
Moskalenko (talk | contribs) |
|||
| (21 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | { | + | {|align=right |
| − | + | |__TOC__ | |
| − | + | |} | |
| − | + | UF is a high-value target for attacks designed to steal research data and intellectual discoveries. Since adopting multi-factor authentication, UF has seen a 99.7% decrease in compromised accounts. MFA prevents unauthorized access to your HiPerGator account by requiring a second authentication method in addition to your GatorLink credentials, such as your mobile device. A malicious agent - whether a person or an automated mechanism - trying to compromise your account is far less likely to gain access to both the knowledge of your credentials and the physical factor necessary to authenticate. You will need to [https://it.ufl.edu/2fa/ sign up for Duo Authentication]. | |
| − | |||
| − | UF is a high-value target for attacks designed to steal research data and intellectual discoveries | ||
=== How Does This Change the User Experience? === | === How Does This Change the User Experience? === | ||
| − | + | Users will see a text menu asking them to select an MFA method as the second step during SSH authentication. Available methods are based on what you have configured in the [https://account.it.ufl.edu/2FA/enrollDevice My Two-Factor page] . Anyone who has used other UF services, like myUFL or ONE.UF, will be familiar with this process. In short, you can either enter a Duo code, or select one of the menu options to proceed with that choice. | |
| − | |||
| − | |||
| − | |||
The [https://mediasite.video.ufl.edu/Mediasite/Play/b475e2428e0445138d76b31106c029f51d short video here] demonstrates the process of logging in with an ssh client using a password. After the password is entered, the terminal prompts for a Duo passcode (e.g. 6-digit code from a token or Duo application) or allows you to select from one of your pre-configured MFA options using a numerical selection. | The [https://mediasite.video.ufl.edu/Mediasite/Play/b475e2428e0445138d76b31106c029f51d short video here] demonstrates the process of logging in with an ssh client using a password. After the password is entered, the terminal prompts for a Duo passcode (e.g. 6-digit code from a token or Duo application) or allows you to select from one of your pre-configured MFA options using a numerical selection. | ||
===Using MFA with GUI SFTP Programs=== | ===Using MFA with GUI SFTP Programs=== | ||
| − | We recommend using WinSCP, Bitvise, or Cyberduck SFTP clients. Bitvise is a 'FastPass' approved application | + | We recommend using WinSCP, Bitvise, or Cyberduck SFTP clients. Bitvise is a 'FastPass' approved application to open any sensitive data at UF. |
| − | * WinSCP | + | * WinSCP, Bitvise and Cyberduck work with Duo 2FA out of the box. Bitvise uses [[SSH Multiplexing]] automatically, so you can both perform SFTP transfers and open a terminal in the same ssh session without having to re-authorize. |
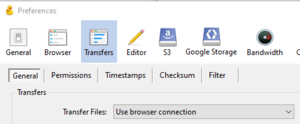
| − | + | * For CyberDuck, to use password-based authentication and only require one MFA push per session (rather than for each file) change the preferences:[[File:CyberDuck transfer browser.png|frameless|right|Screenshot of the CyberDuck options to use Browser Connection]] | |
| − | * | + | ** From the Edit menu > Preferences > Transfers > General. Then select "Use browser connection" from the drop down menu |
| − | === | + | ===Connecting via Terminal to the Command Line=== |
| − | If you | + | If you are using username/password authentication to connect your terminal to the HiPerGator command line then the process does not change much from what it was before, as documented in [[https://help.rc.ufl.edu/doc/HPG_Interfaces HPG Interfaces]] |
| + | After you authenticate with your GatorLink Password you will then be prompted for Duo two-factor authentication. The entire session should look like this: | ||
| + | <div class="mw-collapsible mw-collapsed" style="width:70%; padding: 5px; border: 1px solid gray;"> | ||
| + | ''Expand this section to view example session.'' | ||
| + | <div class="mw-collapsible-content" style="padding: 5px;"> | ||
| − | + | Using username "GatorLinkUsername". | |
| + | Using keyboard-interactive authentication. | ||
| + | Password: | ||
| + | Using keyboard-interactive authentication. | ||
| + | Duo two-factor login for GatorLinkUsername@ufl.edu | ||
| − | |||
| − | |||
| − | |||
| − | |||
Enter a passcode or select one of the following options: | Enter a passcode or select one of the following options: | ||
| − | + | ||
1. Duo Push to XXX-XXX-1234 | 1. Duo Push to XXX-XXX-1234 | ||
2. Phone call to XXX-XXX-1234 | 2. Phone call to XXX-XXX-1234 | ||
| − | + | ||
| − | + | Passcode or option (1-2): | |
| − | Passcode or option (1- | ||
Success. Logging you in... | Success. Logging you in... | ||
| + | </div></div> | ||
| − | === | + | === How can I use SSH keys for authentication? === |
| − | |||
| − | |||
| − | + | See the guide for setup at [[Using SSH Keys To Access HPG | SSH Keys]]. After this, you won't require password, but will still be prompted for Duo MFA as above. | |
| − | |||
| − | |||
| − | |||
| − | |||
==== Using SSH Keys with SFTP clients ==== | ==== Using SSH Keys with SFTP clients ==== | ||
| Line 54: | Line 47: | ||
* Bitvise: See [https://www.bitvise.com/getting-started-public-key-bitvise BitVise documentation]. | * Bitvise: See [https://www.bitvise.com/getting-started-public-key-bitvise BitVise documentation]. | ||
* CyberDuck: See [https://trac.cyberduck.io/wiki/help/en/howto/sftp CyberDuck documentation]. | * CyberDuck: See [https://trac.cyberduck.io/wiki/help/en/howto/sftp CyberDuck documentation]. | ||
| − | |||
| − | === | + | === Using SSH Multiplexing to reduce the number of MFA authentications needed === |
| + | One strategy to reduce the number of times that you need to authenticate using MFA is to use SSH Multiplexing. This opens one connection, which requires an MFA authentication, and then other connections are made through that initial connection. These additional connections do not require MFA. | ||
| + | |||
| + | Please see the details of [[SSH_Multiplexing|SSH Multiplexing configuration on this page]]. | ||
| + | |||
| + | ==Common Errors== | ||
| + | |||
| + | ====Attempting to use SSH Key Authentication, without setting port 2222==== | ||
| + | |||
| + | Without the proper port being specified you will be connected to a login server which will ignore your SSH Key. You will be prompted for a password, but depending on your terminal client and configuration you might not see that prompt. Eventually, multiple failures of the password login will lead to our security software blocking your client due to too many incorrect password attempts, and eventually you may see 'Connection reset by peer' when trying to log in. | ||
| + | |||
| + | Solution: ensure that you're specifying the correct port for SSH Key Authentication as specified above. If you're receiving the 'Connection reset by peer' error message you will need to open a Support Request to ask that your HiPerGator user account be unblocked. | ||
| + | |||
| + | ====Attempting to use SSH Key Authentication, 2222 connects but without SSH Key==== | ||
| + | |||
| + | This is the opposite case to the above issue, in that you're now connecting to a login host which is expecting an SSH Key file but never sending one. A number of invisible errors will happen behind the scenes, and you will eventually see an error message similar to "Server sent: public key" | ||
| + | |||
| + | Solution: Ensure that your connection command line or SSH config file are correct as per the above sections, and that you really do intend to use SSH Key Authentication instead of manually typing a password. If so, then please refer to [[Using_SSH_Keys_To_Access_HPG]] and/or open a Support Request for assistance with setting up SSH Key Authentication. | ||
| + | |||
| + | ====Attempting to log in without having enrolled in MFA==== | ||
| + | |||
| + | Upon login you'll receive an error stating "Not Enrolled". | ||
| − | + | Solution: You will need to sign up for Duo Authentication. There is a minimal chance that a misconfiguration in our system could be producing this error, so if you are certain that your GatorLink account has been signed up for Duo Authentication then open a Support Request stating that you're receiving the 'Not Enrolled' error when trying to log in. | |
| − | |||
| − | |||
Latest revision as of 21:10, 14 July 2023
UF is a high-value target for attacks designed to steal research data and intellectual discoveries. Since adopting multi-factor authentication, UF has seen a 99.7% decrease in compromised accounts. MFA prevents unauthorized access to your HiPerGator account by requiring a second authentication method in addition to your GatorLink credentials, such as your mobile device. A malicious agent - whether a person or an automated mechanism - trying to compromise your account is far less likely to gain access to both the knowledge of your credentials and the physical factor necessary to authenticate. You will need to sign up for Duo Authentication.
How Does This Change the User Experience?
Users will see a text menu asking them to select an MFA method as the second step during SSH authentication. Available methods are based on what you have configured in the My Two-Factor page . Anyone who has used other UF services, like myUFL or ONE.UF, will be familiar with this process. In short, you can either enter a Duo code, or select one of the menu options to proceed with that choice.
The short video here demonstrates the process of logging in with an ssh client using a password. After the password is entered, the terminal prompts for a Duo passcode (e.g. 6-digit code from a token or Duo application) or allows you to select from one of your pre-configured MFA options using a numerical selection.
Using MFA with GUI SFTP Programs
We recommend using WinSCP, Bitvise, or Cyberduck SFTP clients. Bitvise is a 'FastPass' approved application to open any sensitive data at UF.
- WinSCP, Bitvise and Cyberduck work with Duo 2FA out of the box. Bitvise uses SSH Multiplexing automatically, so you can both perform SFTP transfers and open a terminal in the same ssh session without having to re-authorize.
- For CyberDuck, to use password-based authentication and only require one MFA push per session (rather than for each file) change the preferences:
- From the Edit menu > Preferences > Transfers > General. Then select "Use browser connection" from the drop down menu
Connecting via Terminal to the Command Line
If you are using username/password authentication to connect your terminal to the HiPerGator command line then the process does not change much from what it was before, as documented in [HPG Interfaces] After you authenticate with your GatorLink Password you will then be prompted for Duo two-factor authentication. The entire session should look like this:
Expand this section to view example session.
Using username "GatorLinkUsername". Using keyboard-interactive authentication. Password: Using keyboard-interactive authentication. Duo two-factor login for GatorLinkUsername@ufl.edu
Enter a passcode or select one of the following options:
1. Duo Push to XXX-XXX-1234 2. Phone call to XXX-XXX-1234
Passcode or option (1-2): Success. Logging you in...
How can I use SSH keys for authentication?
See the guide for setup at SSH Keys. After this, you won't require password, but will still be prompted for Duo MFA as above.
Using SSH Keys with SFTP clients
- WinSCP: See WinSCP documentation.
- Bitvise: See BitVise documentation.
- CyberDuck: See CyberDuck documentation.
Using SSH Multiplexing to reduce the number of MFA authentications needed
One strategy to reduce the number of times that you need to authenticate using MFA is to use SSH Multiplexing. This opens one connection, which requires an MFA authentication, and then other connections are made through that initial connection. These additional connections do not require MFA.
Please see the details of SSH Multiplexing configuration on this page.
Common Errors
Attempting to use SSH Key Authentication, without setting port 2222
Without the proper port being specified you will be connected to a login server which will ignore your SSH Key. You will be prompted for a password, but depending on your terminal client and configuration you might not see that prompt. Eventually, multiple failures of the password login will lead to our security software blocking your client due to too many incorrect password attempts, and eventually you may see 'Connection reset by peer' when trying to log in.
Solution: ensure that you're specifying the correct port for SSH Key Authentication as specified above. If you're receiving the 'Connection reset by peer' error message you will need to open a Support Request to ask that your HiPerGator user account be unblocked.
Attempting to use SSH Key Authentication, 2222 connects but without SSH Key
This is the opposite case to the above issue, in that you're now connecting to a login host which is expecting an SSH Key file but never sending one. A number of invisible errors will happen behind the scenes, and you will eventually see an error message similar to "Server sent: public key"
Solution: Ensure that your connection command line or SSH config file are correct as per the above sections, and that you really do intend to use SSH Key Authentication instead of manually typing a password. If so, then please refer to Using_SSH_Keys_To_Access_HPG and/or open a Support Request for assistance with setting up SSH Key Authentication.
Attempting to log in without having enrolled in MFA
Upon login you'll receive an error stating "Not Enrolled".
Solution: You will need to sign up for Duo Authentication. There is a minimal chance that a misconfiguration in our system could be producing this error, so if you are certain that your GatorLink account has been signed up for Duo Authentication then open a Support Request stating that you're receiving the 'Not Enrolled' error when trying to log in.