Authentication With MFA
Why is This Happening?
UF is a high-value target for attacks designed to steal research data and intellectual discoveries. This change is part of our ongoing efforts to strengthen the university’s security posture. Since adopting multi-factor authentication, UF has seen a 99.7% decrease in compromised accounts. MFA prevents unauthorized access to your HiPerGator account by requiring a second authentication method in addition to your GatorLink credentials. Think of the username and password as something that you know and a second factor as something you have e.g. a mobile device with a DUO app that MFA can 'push' a request to confirm your login to or a phone number MFA can call. A malicious agent - whether a person or an automated mechanism - trying to compromise your account is far less likely to gain access to both the knowledge of your credentials and the physical factor necessary to authenticate.
How Does This Change the User Experience?
Once implemented, users will see a text menu asking them to select an MFA method as the second step during SSH authentication. Available methods are based on what you have configured in the My Two-Factor page . Anyone who has used other UF services, like myUFL or the UF VPN, will be familiar with this process. In short, you can either enter a Duo code, or select one of the menu options to proceed with that choice.
The short video here demonstrates the process of logging in with an ssh client using a password. After the password is entered, the terminal prompts for a Duo passcode (e.g. 6-digit code from a token or Duo application) or allows you to select from one of your pre-configured MFA options using a numerical selection.
What if I Don't have Duo MFA Enabled?
If your account is not registered with UF's Duo MFA service, you will see an error like this:
We're sorry, access is not allowed because you are not enrolled. Please contact your organization's IT help desk for assistance.
You will need to sign up for Duo Authentication.
Using MFA with GUI SFTP Programs
We recommend using WinSCP, Bitvise, or Cyberduck SFTP clients. Bitvise is a 'FastPass' approved application for open and sensitive data at UF.
- WinSCP, Bitvise and Cyberduck work with Duo 2FA out of the box. Bitvise uses SSH Multiplexing automatically, so you can both perform SFTP transfers and open a terminal in the same ssh session without having to re-authorize.
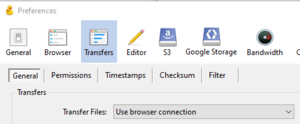
- For CyberDuck, to use password-based authentication and only require one MFA push per session (rather than for each file) change the preferences:
- From the Edit menu > Preferences > Transfers > General
- Select "Use browser connection" from the drop down menu
- FileZilla requires additional configuration. First of all, the Quickconnect mode will not work as it only uses the 'Normal' logon type, which doesn't work with 2FA. For password authentication with 2FA you must set up a connection profile in site manager with an 'Interactive' Logon Type. In addition, set the number of simultaneous connections to '1' in the Transfer Settings for the site or you will get a Duo prompt for each file transfer. If you want to use key authentication with FileZilla you'll have to load a working key into an SSH agent like 'pageant' and use the 'Interactive' logon type.
How can I use SSH keys for authentication?
If you have setup SSH key-based authentication, you will need to configure your client to connect to hpg.rc.ufl.edu using port 2222. You will still be prompted for Duo MFA as above. See the examples below.
SSH Key Authentication from the Command Line
ssh -p 2222 GatorLink@hpg.rc.ufl.edu SSH-Key Auth (GatorLink@hpg.rc.ufl.edu) Duo two-factor login for GatorLink@ufl.edu Enter a passcode or select one of the following options: 1. Duo Push to XXX-XXX-1234 2. Phone call to XXX-XXX-1234 3. Phone call to XXX-XXX-1234 Passcode or option (1-3): 1 Success. Logging you in...
SSH Key Authentication Using a SSH Config File
If you are using an SSH config file (e.g. ~/.ssh/config), add the PORT option:
Host hpg HostName hpg.rc.ufl.edu User GatorLink Port 2222 IdentityFile ~/.ssh/id_rsa
Using SSH Keys with SFTP clients
- WinSCP: See WinSCP documentation.
- Bitvise: See BitVise documentation.
- CyberDuck: See CyberDuck documentation.
- FileZilla: See FileZilla documentation.
Using SSH Multiplexing to reduce the number of MFA authentications needed
One strategy to reduce the number of times that you need to authenticate using MFA is to use SSH Multiplexing. This opens one connection, which requires an MFA authentication, and then other connections are made through that initial connection. These additional connections do not require MFA.
Please see the details of SSH Multiplexing configuration on this page.